 |
| "This Just In" |
|
|
|
| The Story ... Begins .....Below |
THE NEW YORK TIMES
has reported that a
VAST COMPUTER CONSPIRACY
has looted computers in 103 Countries and even hit the Dalai Lama!
WHODUNNIT?
"Country of Interest" Numero Uno:
"C H I N A"
|
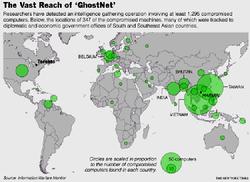 |
| Where Did They Hit? Click Image to Enlarge |
|
|
HOW IT ALL BEGAN ....
THE DALAI LAMA ASKEDCanadian Researchers from the Munk Center for International Studies at the University of Toronto to check his computers for spyware. They found the grand-daddy of spyware ....
"GHOSTNET"At least 1295 computers in 103 countries worth of a "GhostNet" !
- Their findings: In less than 2 years computers in embassies, foreign ministries, government offices, and the Dalai Lama's Tibetan Exile centers in India, Brussels, London, & New York.
- Supposedly the closest GhostNet got to the U.S. computers was a NATO computer and the Indian Embassy in Washington, DC.
THE MALWARE TECHNIQUE USED?"WHALING"
- → It can turn on the camera and audio-recording functions of an infected computer, enable its monitors to see and hear what goes on around it.
"Can You Say Big Brother?"
- When the Chinese caught wind of something they didn't like; they would send out ....... "Operatives" .....
- To "Discourage" the offending persons or "Derail" the offending activites.
- THE "FBI" has declined comment to the Toronto Researchers.
- THE CHINESE deny everything.
Gee, wonder who else cares what Tibetan Exile Groups are up to?
- HOWEVER ..... Is it merely coincidence that when a Chinese version of Skype was linked to a Chinese government operation that it was used for eavesdropping on users' IM sessions?
OR:
|
"THE DASHBOARD"
- A control panel is reached with any standard web browser that lets the GhostNet User use & control the infected GhostNet Network.
- Infection happens when someone clicks on a web link in an e-mail that takes the victim to a "poisonous site"..... OR: The victim clicks on a document attached to to an e-mail message that lets the malware secretly install software deep in the victim's operating system.
- The Researchers found 4 control servers. 3 were in different provinces in China: Hainan, Guangdong and Sichuan. The 4th was at a Web-Hosting Company based in ..... Southern California! "Oooops!"
|
 |
| U.S Electricity Grid Hit by Cyberspies |
|
| " GOOD OR SPECIAL INTEL"
- Sleeper Software Programs have been slipped into the U.S. Electrical Grid. Spies from China, Russia, & other unnamed countries. These type of Intrusions are growing and their purpose appears to have "things in place" to be used when "useful".
- Electricity, Water, and Sewage systems are all at risk. And; so are nuclear power plants and even financial networks.
- The goal is to disrupt U.S. infrastructure prior to war or during war.
- The "GRID" is made up of 3 networks. But among those networks; the intrusions were detected not by ther companies in charge of the networks ... but by U.S. Intel Agencies.
|
A Little Update "Just FYI":
Threat From Clampi Trojan Virus to
Online Banking
- This Trojan monitors more than 4500 finance related websites in Britain & the U.S. and targets Windows Operating Systems. The list includes:
- Banks
- Credit Card Companies
- Online Casinos
- E-mail
- Wire Transfer Services
- Retail Sites
- Utliities
- Share Brokerages
- Mortgage Lenders
- Government Sites
- Most of the sites are small to medium sized businesses and more than 1 in 40 of the infected computers have been in Britain. Mostly English-speaking countries are being targeted.
- FOR EXAMPLE: $75,000 was stolen from an Auto Parts Store in Gainesville, GA.; while in Sands Spring, Oklahoma, online banking details for the public school district were stolen... and thru submitting phony payroll vouchers, they made off with more than $150,000. They also got more than $700,000 from the Western Beaver School District.
- There is an uptick of nasty stuff on even popular search engines, blogs, online magazines and News sites. The New York Times found a nasty virus in one of the ads placed on their site.
- Variants of Clampi ... Ligats or llomo ... have been around since 2005. This one has been around since July... but a 2nd wave is emerging.
TIPS?
(The Usual)
- Use credit cards, not debit cards
- Watch out for suspicious links in e-mails, IM's & Social Sites
- Get good Security software and keep it updated
- Make sure you have browser protection
- Use a strong password for Wi-Fi connections
- If you have been infected ... change all passwords...learn how to create a "good" password .
|
Another Update: Just "FYI" February 18, 2010
By Siobhan Gorman
Wall Street Journal
- Hackers in Europe and China successfully broke into computers at nearly 2,500 companies and government agencies over the last 18 months in a coordinated global attack that exposed vast amounts of personal and corporate secrets to theft, according to a computer-security company that discovered the breach.
- The damage from the latest cyberattack is still being assessed, and affected companies are still being notified. But data compiled by NetWitness, the closely held firm that discovered the breaches, showed that hackers gained access to a wide array of data at 2,411 companies, from credit-card transactions to intellectual property.
- The hacking operation, the latest of several major hacks that have raised alarms for companies and government officials, is still running and it isn't clear to what extent it has been contained, NetWitness said. Also unclear is the full amount of data stolen and how it was used. Two companies that were infiltrated, pharmaceutical giant Merck & Co. and Cardinal Health Inc., said they had isolated and contained the problem.
- Starting in late 2008, hackers operating a command center in Germany got into corporate networks by enticing employees to click on contaminated Web sites, email attachments or ads purporting to clean up viruses, NetWitness found.
- In more than 100 cases, the hackers gained access to corporate servers that store large quantities of business data, such as company files, databases and email.
- They also broke into computers at 10 U.S. government agencies. In one case, they obtained the user name and password of a soldier's military email account, NetWitness found. A Pentagon spokesman said the military didn't comment on specific threats or intrusions.
- At one company, the hackers gained access to a corporate server used for processing online credit-card payments. At others, stolen passwords provided access to computers used to store and swap proprietary corporate documents, presentations, contracts and even upcoming versions of software products, NetWitness said.
- Data stolen from another U.S. company pointed to an employee's apparent involvement in criminal activities; authorities have been called in to investigate, NetWitness said. Criminal groups have used such information to extort sensitive information from employees in the past.
- The spyware used in this attack allows hackers to control computers remotely, said Amit Yoran, chief executive of NetWitness. NetWitness engineer Alex Cox said he uncovered the scheme Jan. 26 while installing technology for a large corporation to hunt for cyberattacks.
- That discovery points to the growing number of attacks in recent years that have drafted computers into cyber armies known as botnets—intrusions not blocked by standard antivirus software. Researchers estimate millions of computers are conscripted into these armies.
- "It highlights the weaknesses in cyber security right now," said Adam Meyers, a senior engineer at government contractor SRA International Inc. who reviewed the NetWitness data. "If you're a Fortune 500 company or a government agency or a home DSL user, you could be successfully victimized."
- Disclosure of the attack comes on the heels of Google Inc.'s allegation that it and more than 20 other companies were breached by Chinese hackers. This operation appears to be more far-reaching, infiltrating some 75,000 computers and touching 196 countries. The highest concentrations of infected computers are in Egypt, Mexico, Saudi Arabia, Turkey and the U.S.
- NetWitness, based in Herndon, Va., said it was sharing information with the companies infected. Mr. Yoran declined to name them. The company provides computer security for U.S. government agencies and companies. Mr. Yoran is a former Air Force officer who also served as cyber security chief at the Department of Homeland Security.
“The key is not to pour money into protecting information, but to develop a global approach to neutralizing its value. By creating secrets, we have created value, which is pursued by opportunists.”—John M. Brock
- Besides Merck and Cardinal Health, people familiar with the attack named several other companies infiltrated, including Paramount Pictures and software company Juniper Networks Inc.
- Merck said in a statement that one computer had been infected. It said it had isolated the attack and that "no sensitive information was compromised."
- Cardinal said it removed the infected computer from its network. Paramount declined to comment. Juniper's security chief, Barry Greene, wouldn't speak about any specific incidents but said the company worked aggressively to counter infections.
- NetWitness, which does extensive work for the U.S. government and private-sector clients, said it was sharing its information with the Federal Bureau of Investigation. The FBI said it received numerous allegations about potential compromises of network systems and responded promptly, in coordination with law-enforcement partners.
- The computers were infected with spyware called ZeuS, which is available free on the Internet in its basic form. It works with the FireFox browser, according to computer-security firm SecureWorks. This version included a $2,000 feature that works with FireFox, according to SecureWorks.
- Evidence suggests an Eastern European criminal group is behind the operation, likely using some computers in China because it's easier to operate there without being caught, said NetWitness's Mr. Yoran.
- There are some electronic fingerprints suggesting the same group was behind a recent effort to dupe government officials and others into downloading spyware via emails purporting to be from the National Security Agency and the U.S. military, NetWitness's Mr. Yoran said.
That attack was described in a Feb. 5 report from the Department of Homeland Security, which said it was issuing an alert to the government and other organizations to "prevent further compromises."
A DHS official said that ZeuS was among the top five reported tools for malware infections.
|
|